Azure AD Authentication Changes
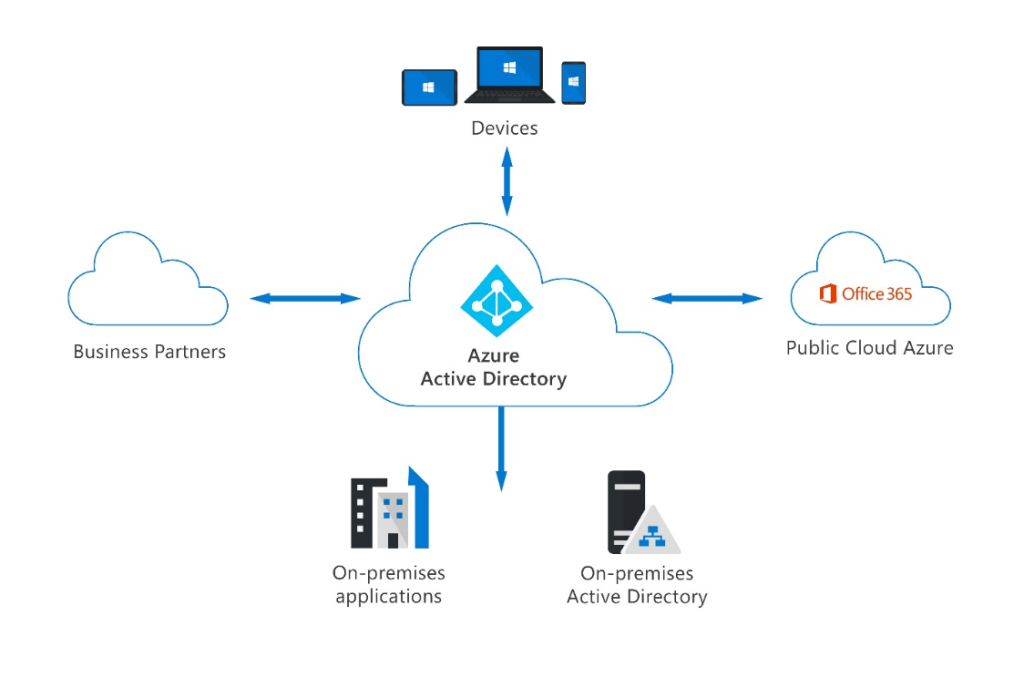
On September 30th, 2024, the legacy multifactor authentication and self-service password reset policies will be deprecated, and you’ll manage all authentication methods in the Authentication Methods policy. Administrators must begin migrating policies from these separate configurations into a single converged policy. Luckily Microsoft has provided a few tools to help Administrators with this migration process.
What is Changing?
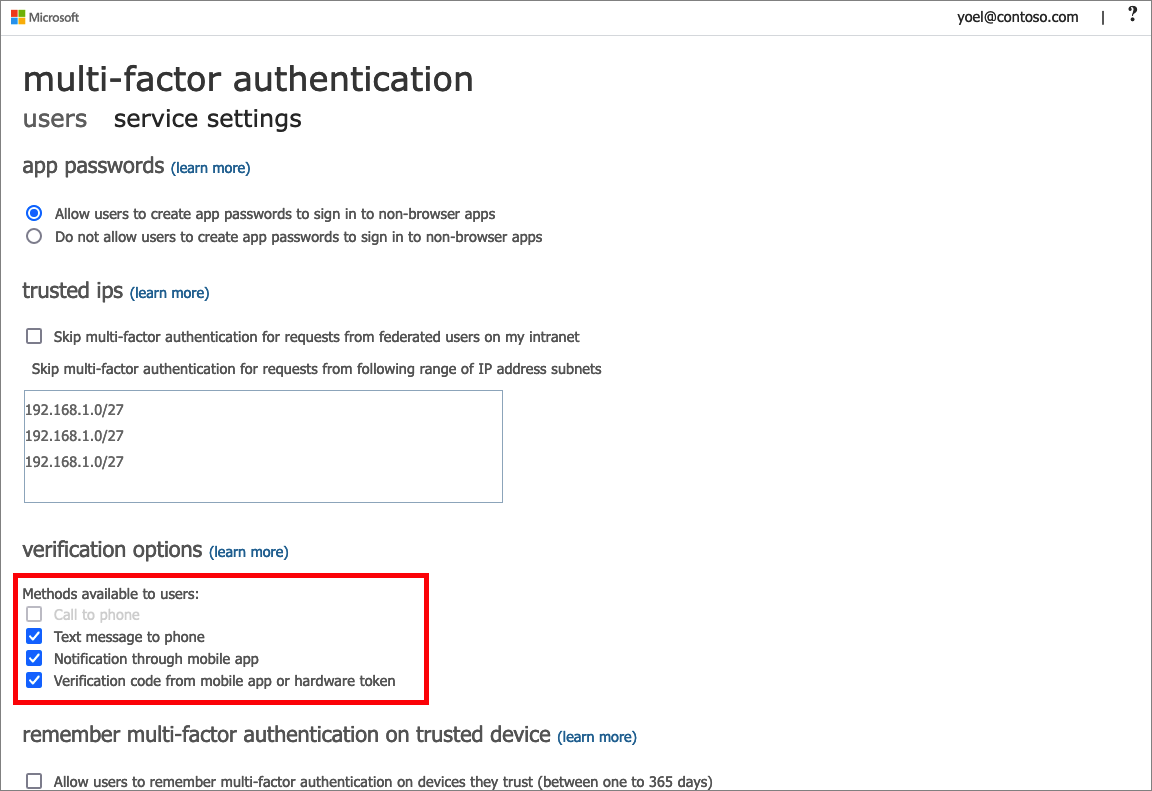
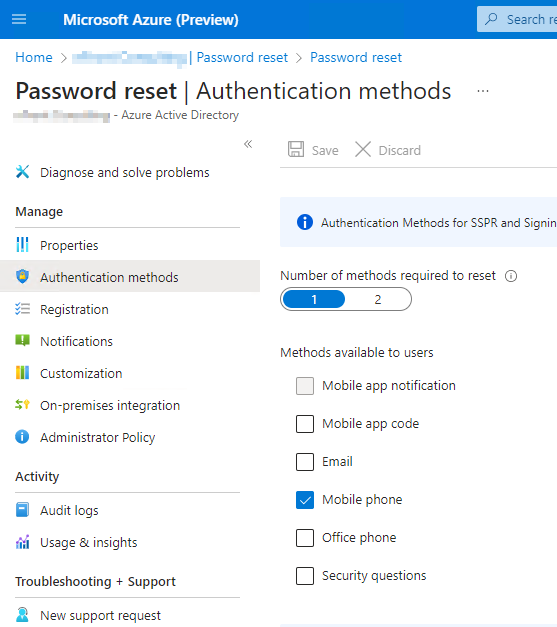
The legacy MFA settings (Azure Active Directory > Users > All users > Per-user MFA > service settings) and the legacy Self-Service Password Reset (SSPR) policies (Azure Active Directory > Users > Password reset > Authentication methods) are being retired in September 2024. In the legacy configuration, MFA and SSPR were separate policies that could be configured differently. This can be a little confusing because many environments were configured similarly, so it didn’t appear to be separate policies. But in some scenarios, this was confusing to end users who had to register Authentication methods like Microsoft Authenticator twice.
The new Authentication methods policy has other methods that aren’t available in the legacy policies, such as FIDO2 security key, Temporary Access Pass, and Azure AD certificate-based authentication. But the primary benefit is that administrators have a single place to manage MFA for authentication and SSPR. And for users, they only have to register once.
Long-time Azure AD Administrators will remember that the Legacy MFA settings existed in a different portal. The settings were on the account.activedirectory.windowsazure.com domain, not the portal.azure.com domain.
Legacy Multi-Factor Authentication Policy
Legacy SSPR Policy
Migrating to a Converged Policy
I will detail the steps to migrate to a converged Authentication Policy, including testing and deploying to all users.
- Document Current State
- Setup Test Users & Groups
- Create Testing Policies
- Disable Legacy for Testers
- Enable for All Users
The different portals needed for the migration are as follows:
Legacy MFA Settings: https://account.activedirectory.windowsazure.com/UserManagement/MfaSettings.aspx
Legacy SSPR Settings: https://portal.azure.com/#view/Microsoft_AAD_IAM/PasswordResetMenuBlade/~/AuthenticationMethods
Authentication Methods: https://portal.azure.com/#view/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade/~/AdminAuthMethods
Document Current Policies
The first step is to determine what methods are currently being used in the two different policies. Browse to the Legacy MFA portal and the Legacy SSPR portal, and document the factors currently being used. You will want to ensure they’re included in the new policies later.
Legacy MFA | Legacy SSPR |
|
|
Setup Test Users & Groups
Create a new AAD Group called “Authentication Methods – Testing” and add test users to it.
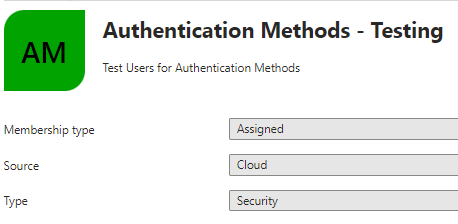
Configure Authentication Methods
Navigate to the new Authentication Methods portal and configure Authentication Methods Policies and general settings.
Policies
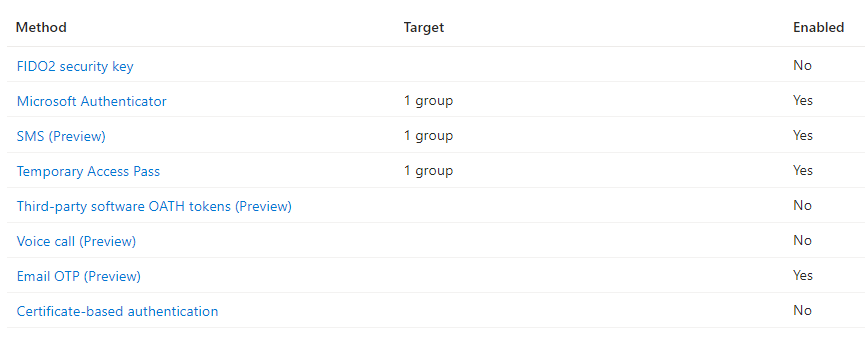
Click on each of these Methods to create a Policy and enable the method. If you need to enable other Methods, use a similar method.
- Microsoft Authenticator
- SMS
- Temporary Access Pass
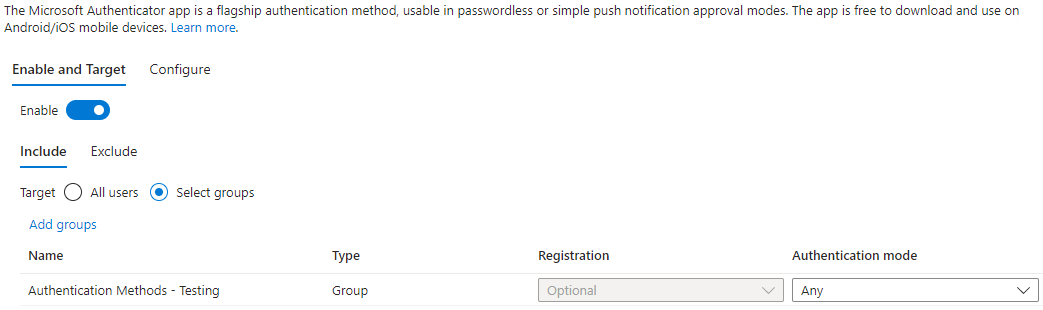
Microsoft Authenticator
Enable and Target
Select Enable, and under Include, select Select Groups and click Add Groups, find the Authentication Methods – Testing group you created earlier.
Change Authentication Mode to Any
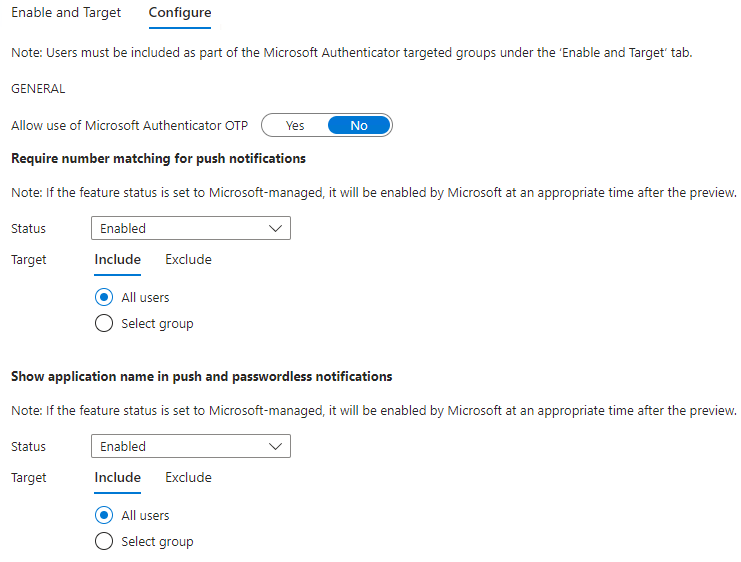
Configure
- Require Number Matching for Push Notifications: Enabled | All Users
- Show Application Name in Push and Passwordless Notifications: Enabled | All Users
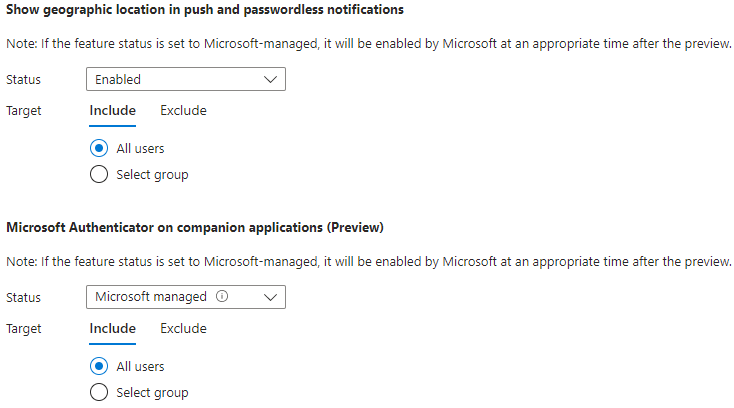
- Show Geographic Location in Push and Passwordless Notifications: Enabled | All Users
- Microsoft Authenticator on Companion Applications: Microsoft Managed | All Users
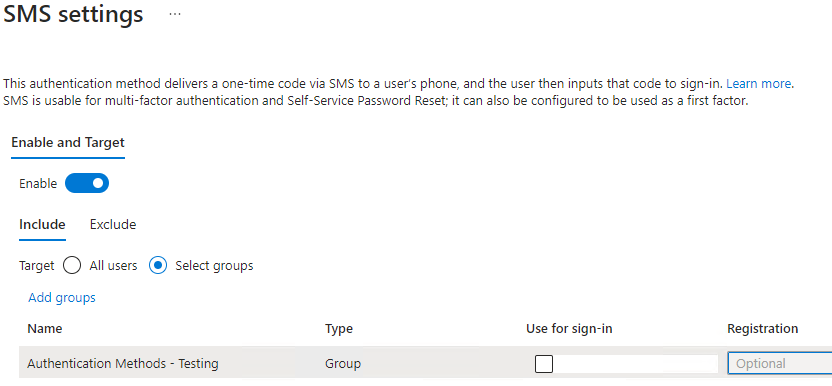
SMS (Preview)
Select Enable, and under Include, select Select Groups and click Add Groups; find the Authentication Methods – Testing group you created earlier.
Note that by default, SMS is not the Primary Method for sign-ins.
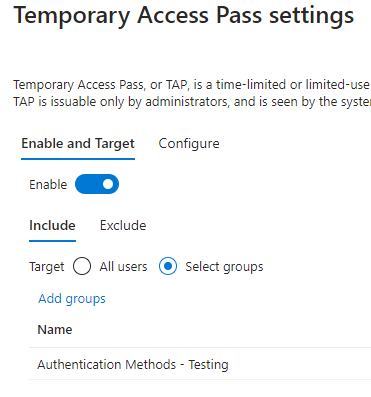
Temporary Access Pass
Enable and Target
Select Enable, and under Include select Select Groups and click Add Groups, find the Authentication Methods – Testing group you created earlier.
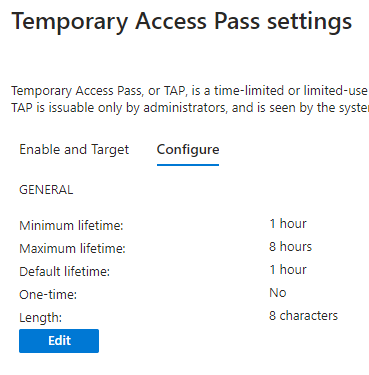
Configure
Leave the default values unless you have a specific need to change them.
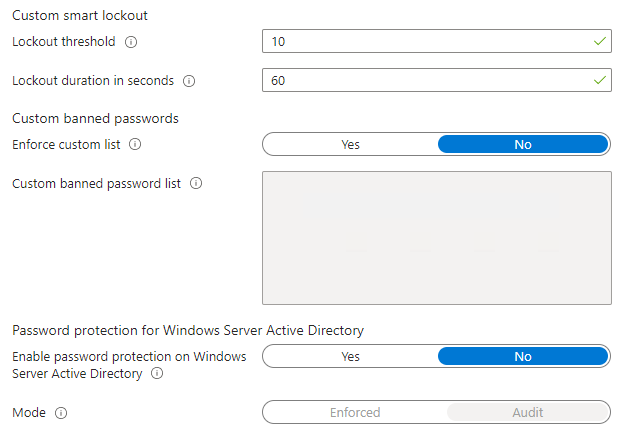
Password protection
Configure password protection settings.
- Lockout Threshold: 10
- Lockout Duration in Seconds: 60
- Custom Banned Passwords: No
- Password Protection for Windows Server Active Directory: No
Authentication Methods Settings
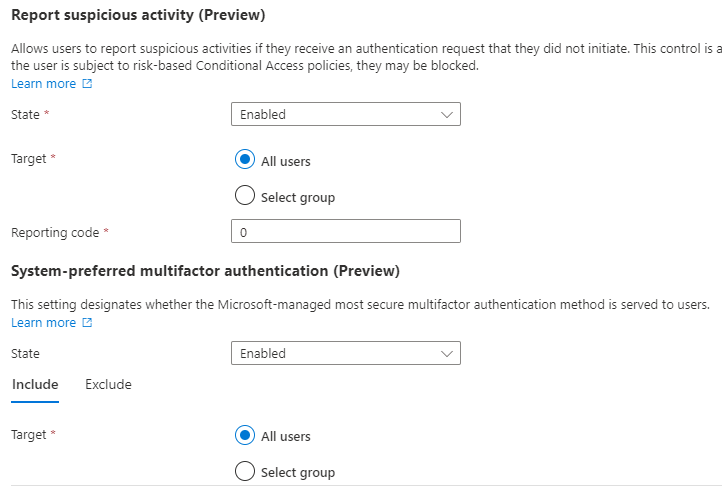
Enable the User reporting of suspicious activity, and enable the system-preferred MFA.
Report suspicious activity
State: Enabled
Target: All users
Reporting Code: 0
System-preferred multifactor authentication
State: Microsoft managed
Target: All users
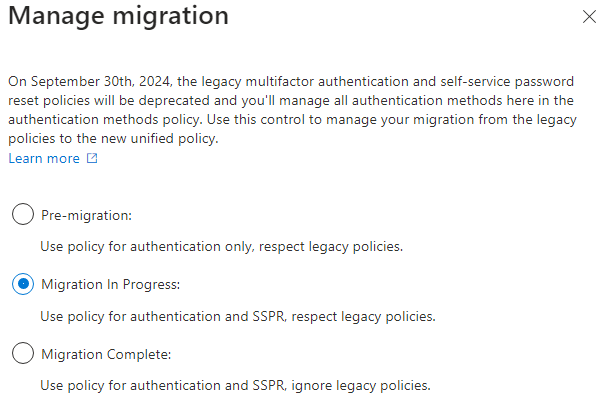
Manage Migration
Change the setting to Migration in Progress and save. This will allow you to test without impacting users.
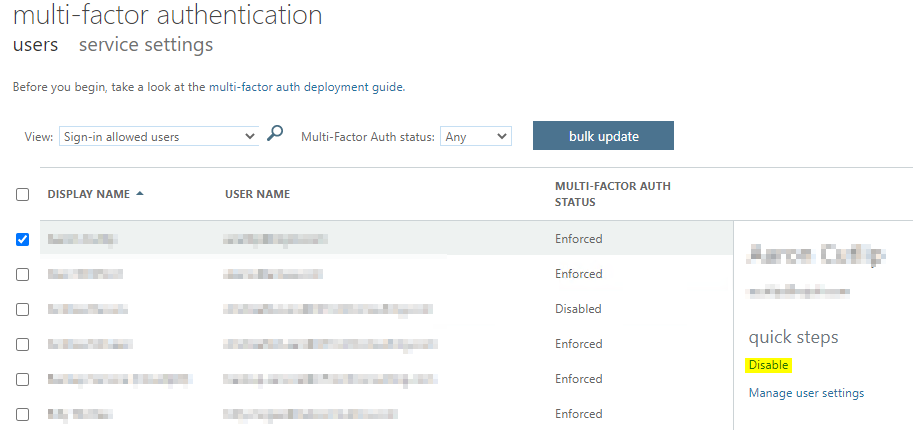
Disable Legacy for Testers
Browse to the Legacy MFA Settings and Disable legacy MFA for the testers.
Ensure that you have a Conditional Access Policy in place that enforces MFA.
Enable for All Users
After you complete testing, you can enable Authentication methods for all users. To complete this step, go through the legacy MFA and SSPR policies and remove each authentication method one by one. Test and validate the changes for each method.
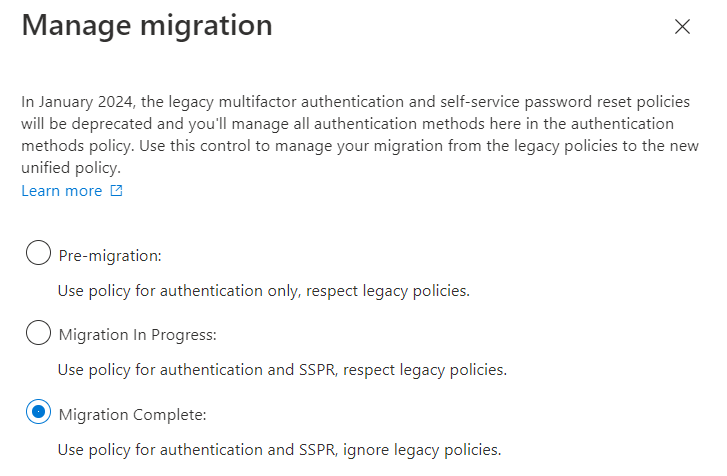
When you determine that MFA and SSPR work as expected and that you no longer need the legacy MFA and SSPR policies, you can change the migration process to Migration Complete. When you save the Manage Migration as Migration Complete, Azure AD will only follow the Authentication methods policy. No changes can be made to the legacy policies if Migration Complete is set, except for security questions in the SSPR policy. If you must return to the legacy policies, you can move the migration state back to Migration in Progress anytime.
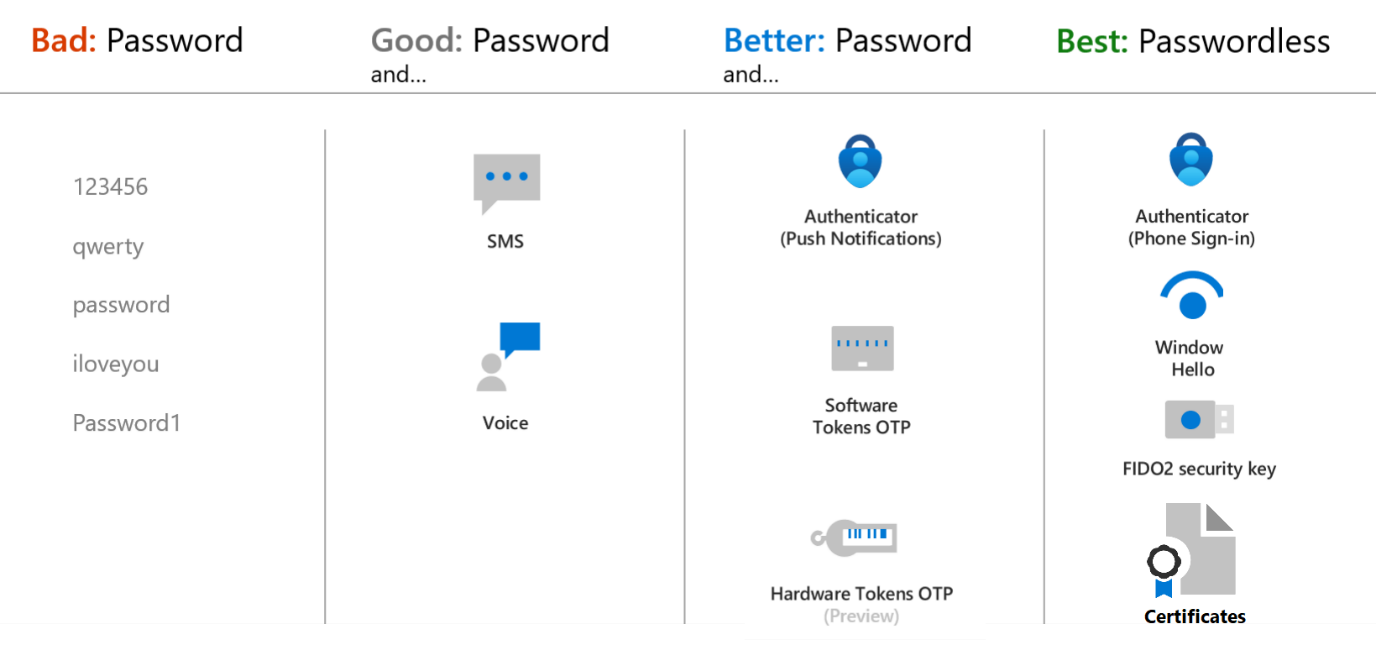
Authentication Strengths
Different Authentication Strengths have different strengths. You may want to consider enabling stronger authentication methods to improve security further.
User Experience
Most of the MFA experience is very similar to the legacy experience. A few things are different.
Registration
New user accounts or existing user accounts that are forced to reregister will see slightly different screens now.
During the first login, users will be prompted to register for MFA.
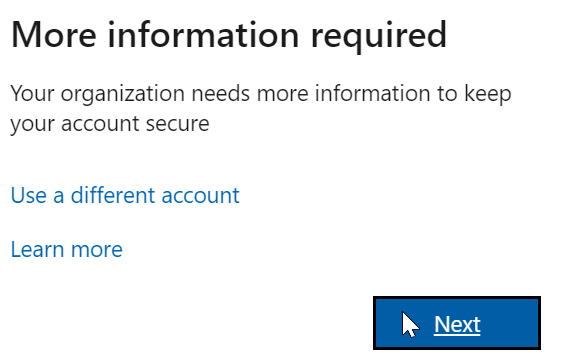
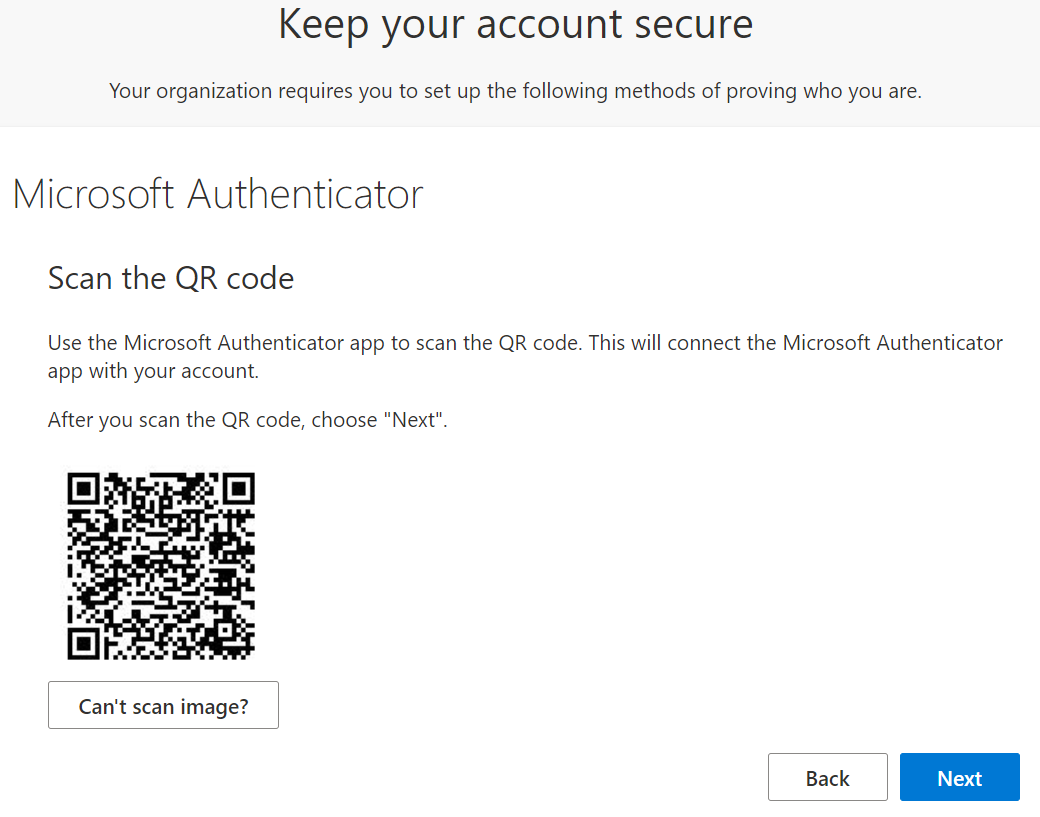
Users will be prompted to configure Microsoft Authenticator, but they can switch to SMS if they want.
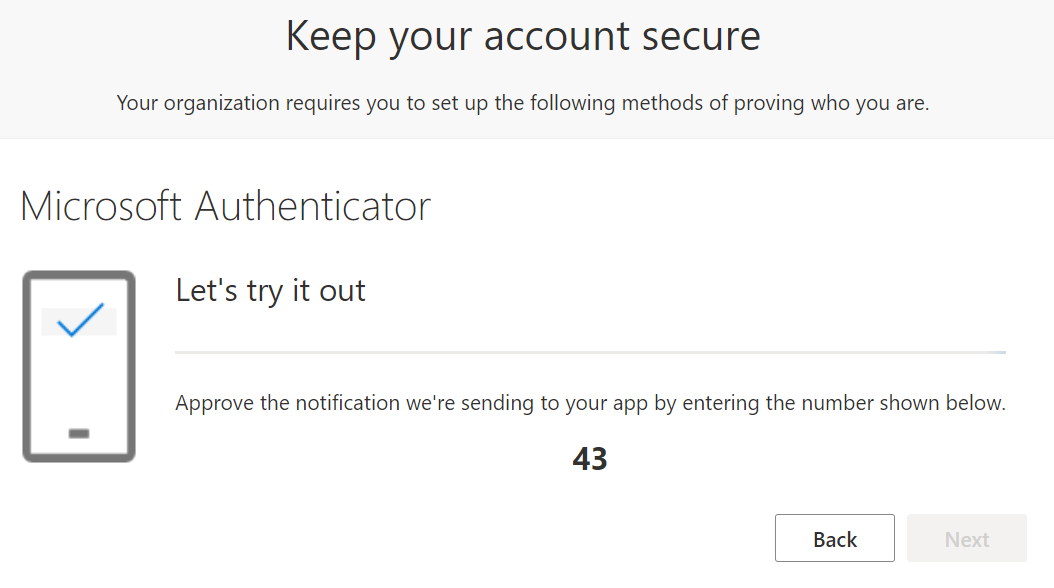
Once the Microsoft Authenticator mobile app has been configured, they will be prompted to confirm. Note that the Number Match is required.
The user will be confirmed.
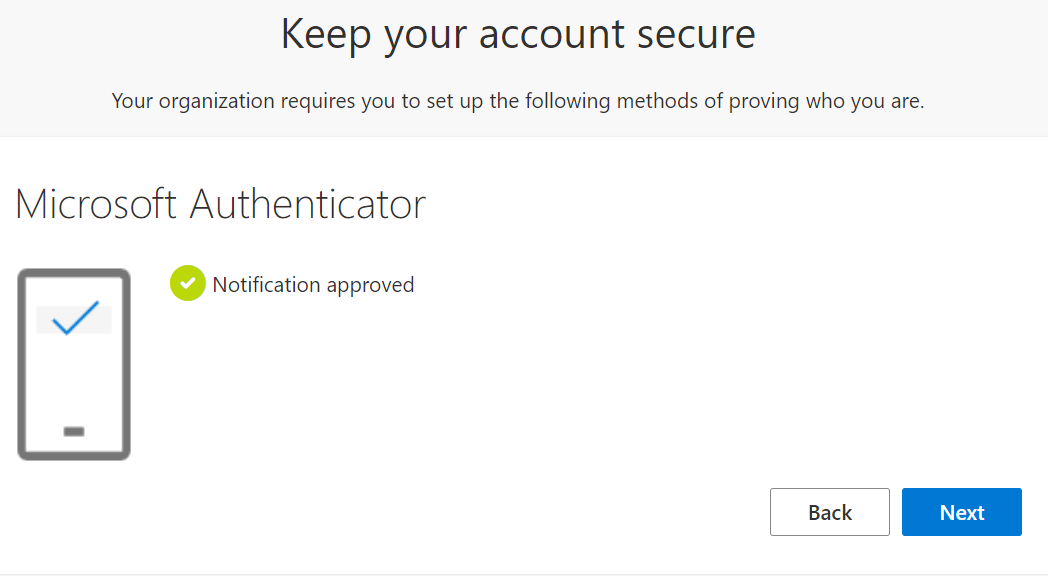
Login Experience
During the user’s login, if they use Microsoft Authenticator, they will see a prompt to use the Authenticator app. But unlike previously, it will provide a number match.
Note that the experience for SMS is unchanged.
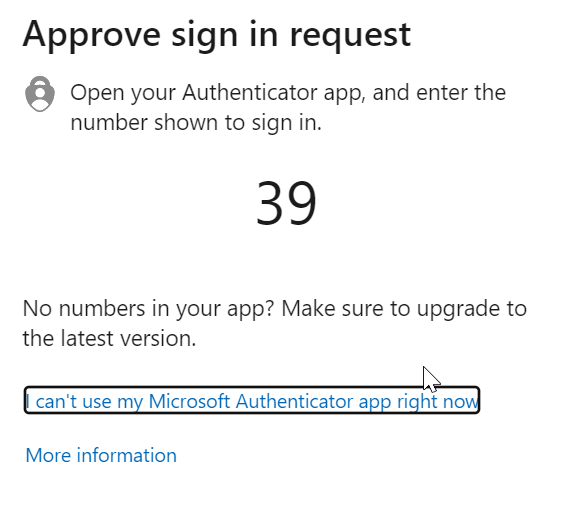
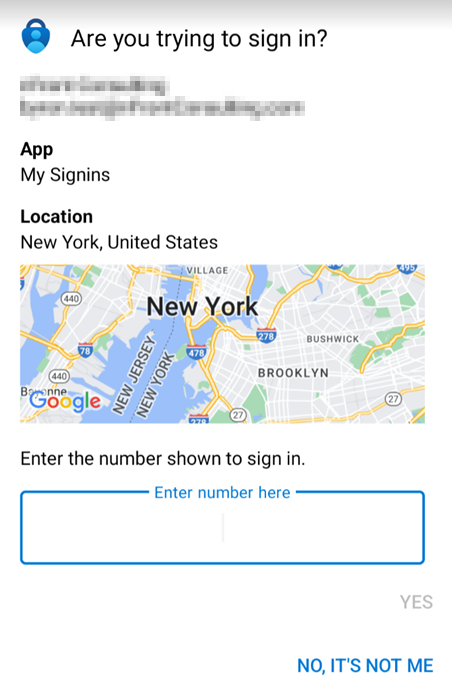
On the user’s mobile device they will be prompted to enter the number match and click YES.
The user is also given the name of the Application that is logging in and the Location of the login.
