2020 has presented an increasing number of challenges for Information Security teams. Some companies have shifted their entire staffs to work from home, and this means some users are not working outside of traditional security controls like Content Filters, Intrustion Prevention Systems, and Next Generation Firewalls. This puts users at greater risk of phishing attacks and credential theft.
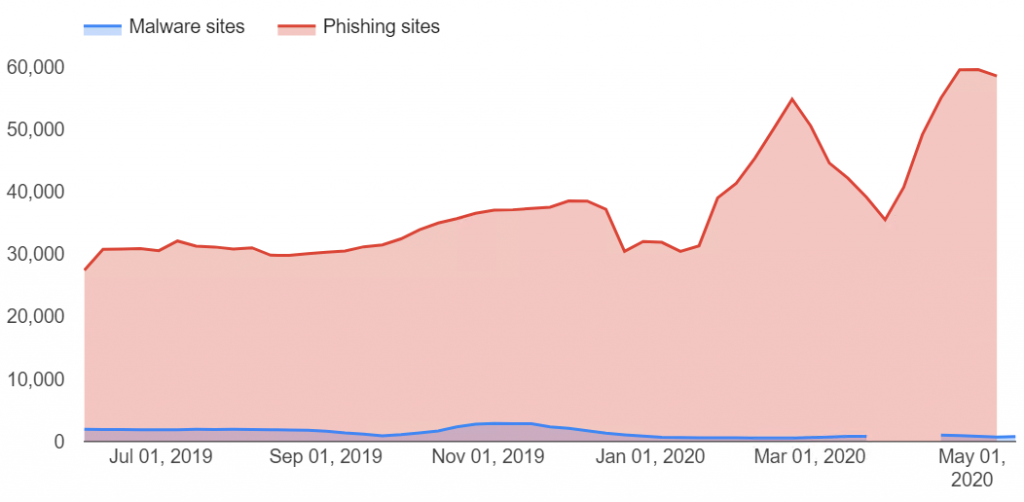
On top of this we know that so far in 2020 attackers are creating an increasing number of phishing websites to lure unspecting users into divulging credentials. Google’s Safe Browsing service showed that the number of phishing websites have just about doubled from 30k in January 2020 to almost 60k in April 2020.
We know that this is a result of attackers wanting to capitalize on the global pandemic and use it as an opportunity to breach companies for financial gain. As a result, organizations must be locking down access as tightly as possible. One option that is often overlooked in IAM systems is blocking logins from foreign countries. If your organization only has domestic users or international users in a few countries, you should block logins from most countries. This will only users to log in from IP addresses associated with your country and block all other logins. Since most attackers are in foreign countries, this is a low cost, low impact control to reduce your exposure to account takeovers.
Blocking Countries in Office 365
The primary method to create geo-location rules in Office 365 is via an Azure Active Directory Conditional Access Rule. Follow these steps to create your block rule.
- To setup geo-location rules, open the Azure Portal and under the Security Section.
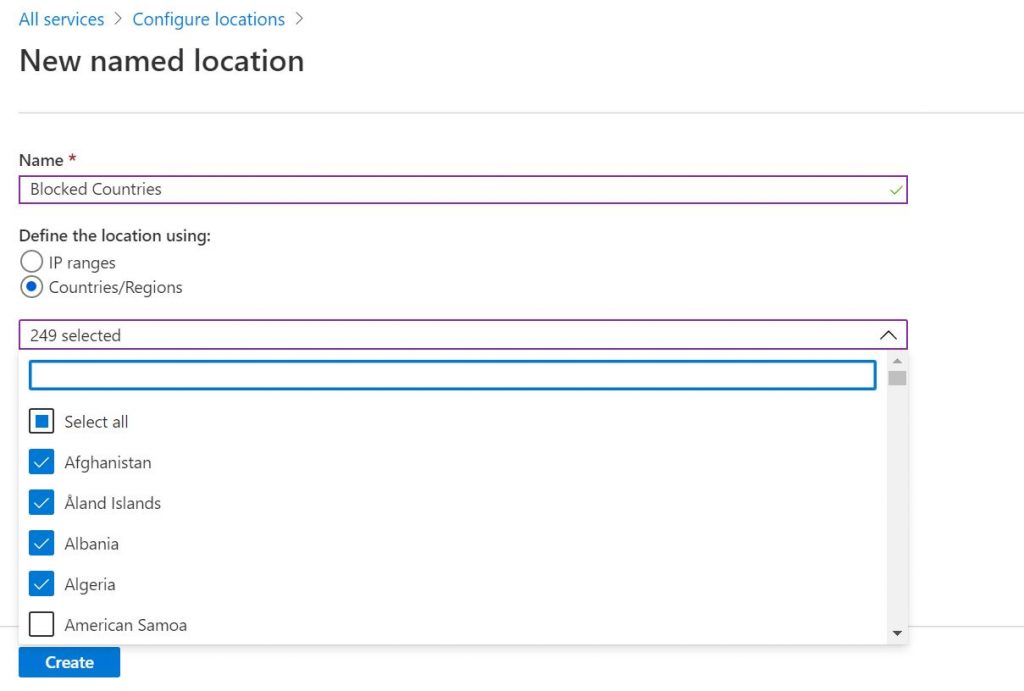
- Create a new named location, call it Blocked Countries. Change the “Define the location using:” option to “Countries/Regions“. Select all the countries that you would never have a user located. Be sure to check the “Include unknown areas” box.
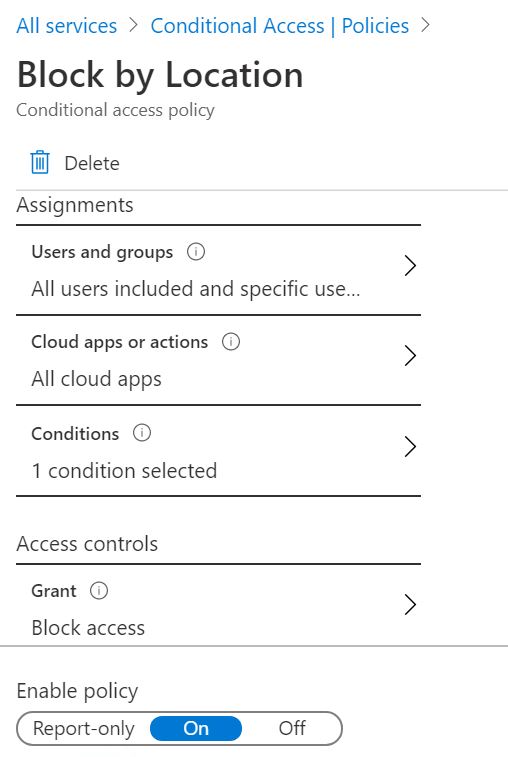
- Go back to Azure Security Services and select the Azure AD Conditional Access icon. Create a new Policy called Block by Location.
Under Users and groups, select All Users.
Under Cloud apps or actions, select All cloud apps.
- Under Conditions, select Locations, select Yes under Configure, select the option for Selected locations. Then select the Blocked Countries named location you created earlier.
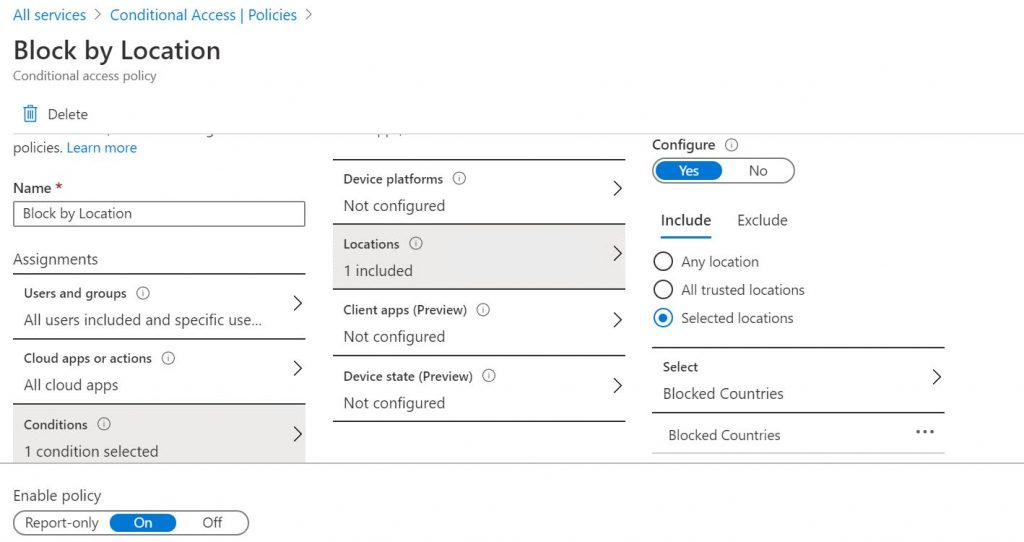
- Under Access Controls, within the Grant section, change it to Block access. Within the Session section, make no changes. Ensure that Enable Policy is set to On, and then Save the policy. The geo-location rules should now be in effect.
Okta and Other IAM Platforms
Other IAM systems like Okta, Auth0, and OneLogin also provide the ability to create Geo-Location Rules. You can easily configure rules to block foreign countries in these platforms from logging into your accounts.
Okta
In Okta follow these steps to setup Geo-location rules. Note before starting you need to submit a case with support to enable geolocation.
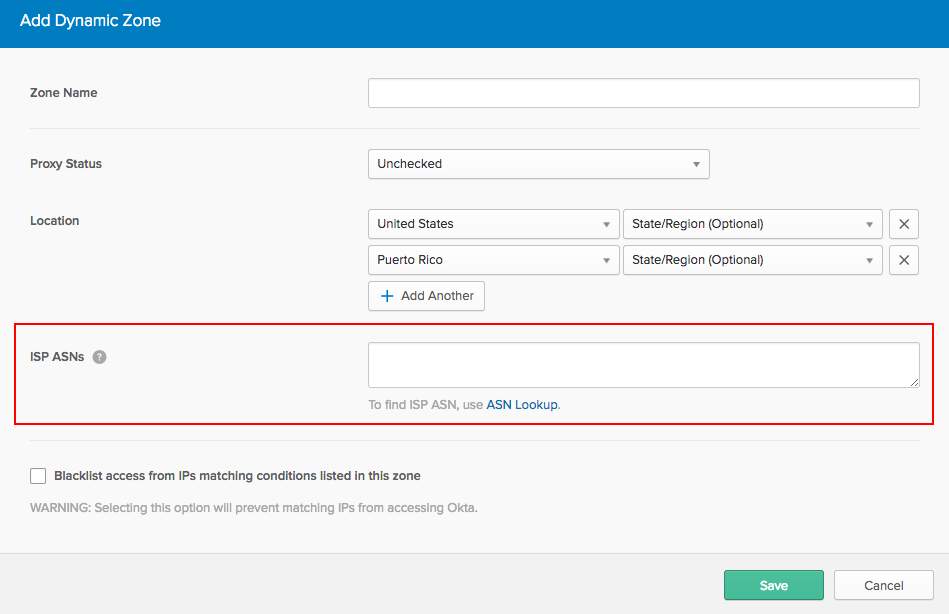
- In your Okta Dashboard go to Security > Networks.
- Click Add Zone > Dynamic Zone.
- Name the zone, Blocked Countries.
- Enter the countries you want to block to the Dynamic Zone.
- Select Blacklist access from IPs listed in this zone to prevent matching IPs from accessing Okta. Click Save.
- Any authentication from an IP in this Dynamic Zone will now fail.
Auth0
Auth0 provides the capability to block certain countries during authentication, but you have to custom create the logic using Auth0 rules. It is certainly not as straight forward as Azure and Okta, but it can be done. This Auth0 post describes the steps needed to create Geo-Location Rules.
OneLogin
OneLogin allows you to create Vigilance Rules that provide geo-location blocking capability. You have to create the rules via the OneLogin API, but it can be done fairly easily. OneLogin has an article that describes how to setup the rules.
Summary
Enabling geo-location rules is a fairly simple method to protect your accounts from unauthorized access. If your not using these kind of rules, you should probably review your options. A few things to keep in mind, if you have users on vacation in another country, you may lock them out. Also these kinds of rules are not a silver bullet. A sophisticated attacker will use a VPN or a cloud virtual machine hosted in your country to get around the geo-location rule, but it will make it more difficult on the majority of attackers.
Credits
Phishing data from Google’s Transparency Report
Photo by Arian Darvishi on Unsplash
