Creating an Analytics Rule for CrowdStrike Detections in Azure Sentinel
If you’re using Azure Sentinel and CrowdStrike, you probably have noticed there’s no native Connector for CrowdStrike events. That can be a little frustrating because if you’re using Sentinel as your Cloud SIEM, not getting next-gen antivirus detections can be operationally challenging. CrowdStrike can also be a rich source of data and events for Sentinel that can drive other Analytics detections in Sentinel. The good news is that it’s not that hard to resolve this gap using CEF forwarding to Azure Sentinel and a custom Analytics rule.
Forwarding CrowdStrike Events to Sentinel
I’m not going to spend a lot of time on how to configure the CrowdStrike log forwarding to Sentinel. CrowdStrike has a pretty good article on how to configure SIEM integration using CEF.
https://www.crowdstrike.com/blog/tech-center/integrate-with-your-siem/
https://docs.microsoft.com/en-us/azure/sentinel/connect-cef-agent?tabs=rsyslog
You need a Linux VM either in Azure or a data center running the CrowdStrike Data Replicator. Install the Azure Syslog Collector and configure the Data Replicator to forward to it. Once this is done, the CrowdStrike events will be forwarded into Azure Sentinel. You can then begin querying those events through Log Analytics using the CommonSecurityLog table.
A basic query to check for the CrowdStrike events would look like this:
CommonSecurityLog | where DeviceVendor == "CrowdStrike" and DeviceProduct == "FalconHost" | where DeviceAction == "Malicious Activity"
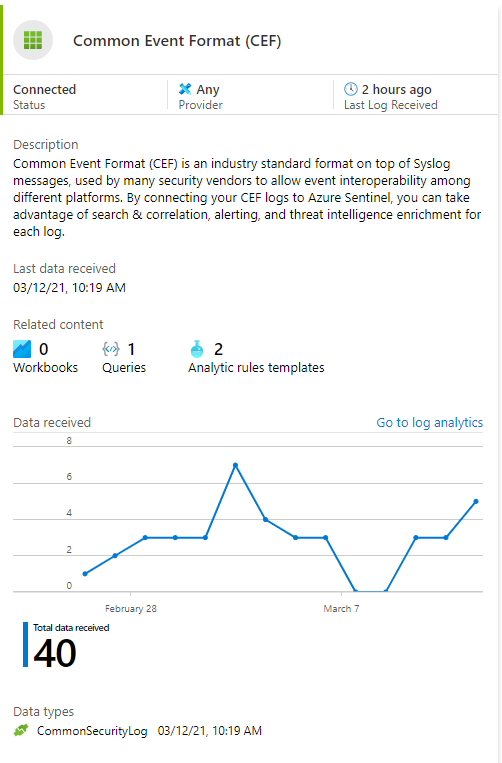
CEF Data Connector
Now that you have the data in Azure Sentinel, you can start configuring it for use. From your Azure Sentinel instance, select Connectors.
Navigate through the list of Connectors and find the Common Event Format (CEF) connector. Ensure that the Connector is enabled and receiving data.
If you generate a test detection in CrowdStrike, you should see it in the Log Analytics Workspace now.
Sentinel has several Analytics Templates for CEF events but nothing specific to CrowdStrike. So we’ll need to create our own Analytics Rule to get Incidents and Alerts.
CrowdStrike Analytics Rule
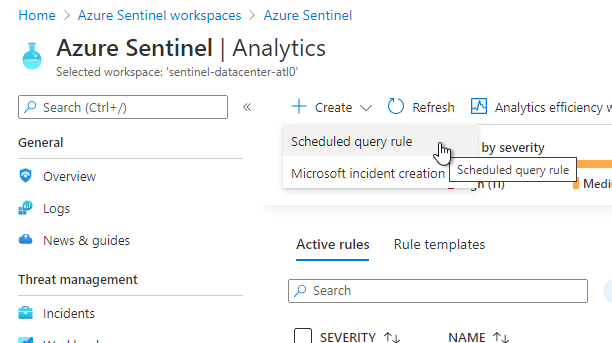
In Azure Sentinel Analytics, select Create and click Scheduled query rule. This will create a new Rule that runs a query on a Schedule and generates Incidents if there any results.
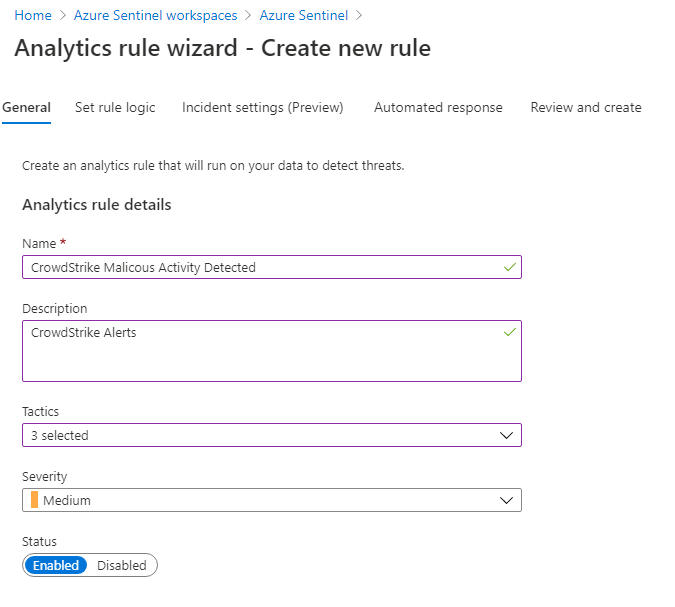
On the General tab, fill in the Name as “CrowdStrike Malicious Activity Detect” and the Description as “CrowdStrike based alerts.” You can change the severity to what is appropriate for your organization, but I think Medium is suitable.
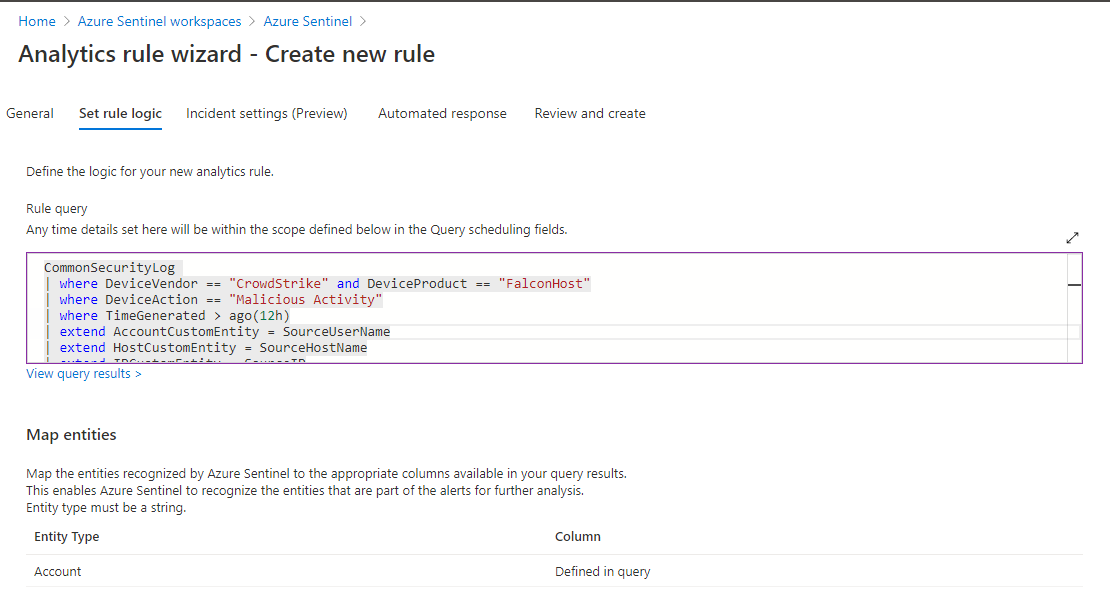
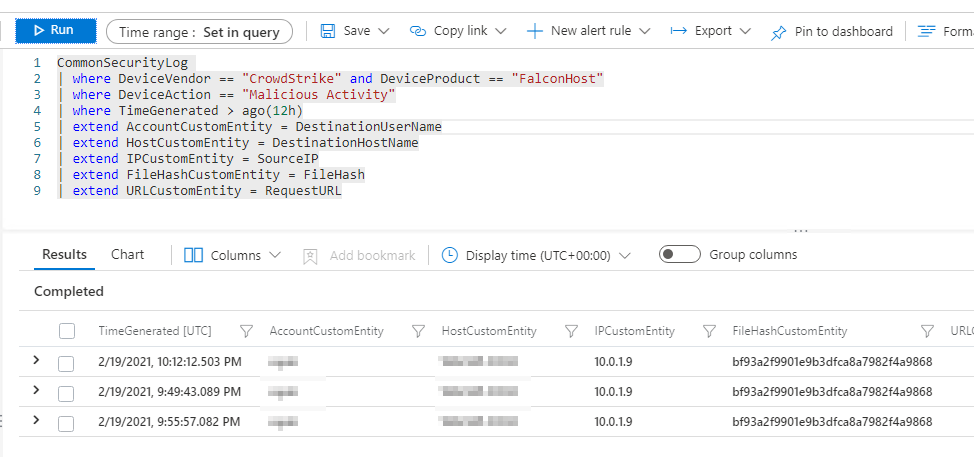
On the Set Rule Logic tab, use the following query. This looks at activity in the less 12 hours for a CrowdStrike event that uses the “Malicious Activity” flag. This will also populate the User Entity Behavior Analytics fields in Sentinel.
CommonSecurityLog | where DeviceVendor == "CrowdStrike" and DeviceProduct == "FalconHost" | where DeviceAction == "Malicious Activity" | where TimeGenerated > ago(12h) | extend AccountCustomEntity = DestinationUserName | extend HostCustomEntity = DestinationHostName | extend IPCustomEntity = SourceIP | extend FileHashCustomEntity = FileHash | extend URLCustomEntity = RequestURL
On the Incident Settings Tab, you can define how frequently it runs. I have it set to run every hour. You may want it to run more regularly to stay on top of potentially malicious activity on endpoints.
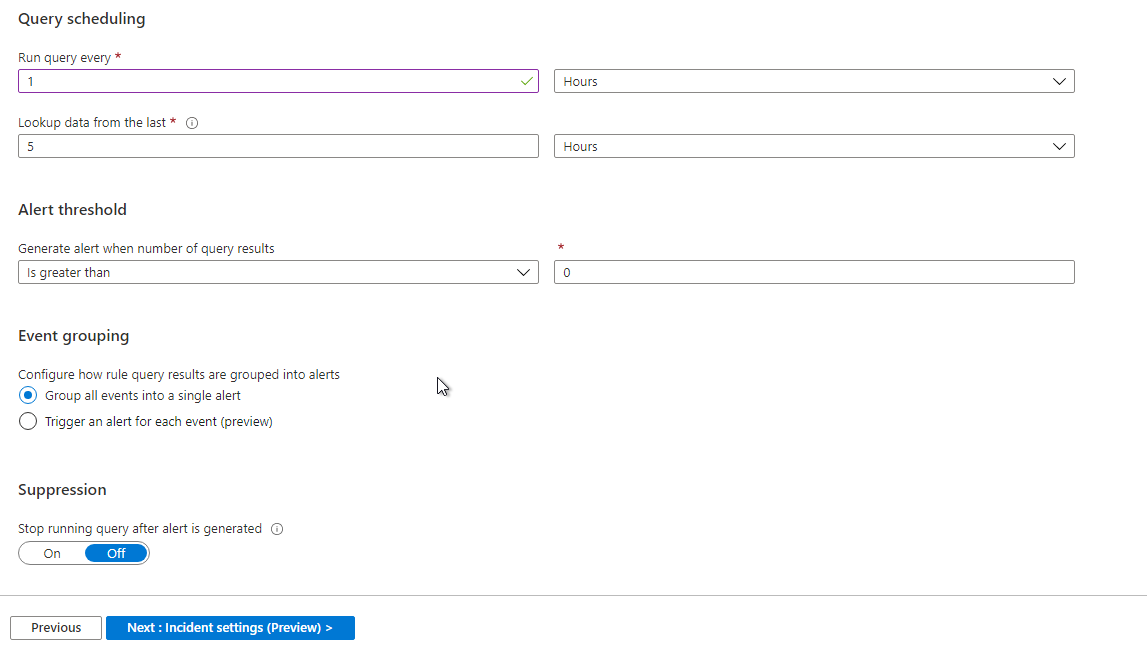
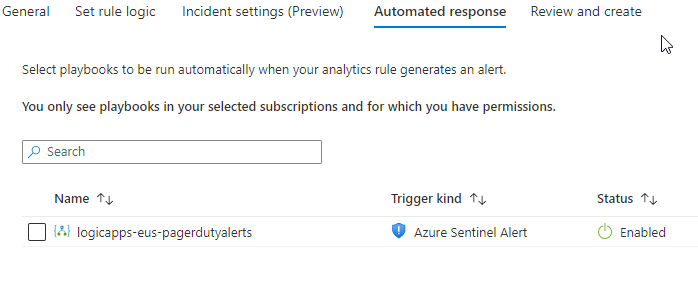
You can select an existing Azure Logic App to run on the Automate Response tab when this Incident gets created. This is very helpful in doing notifications. In this case, I’m using a Logic App that is sending alerts to Pager Duty so they can be pushed to my phone.
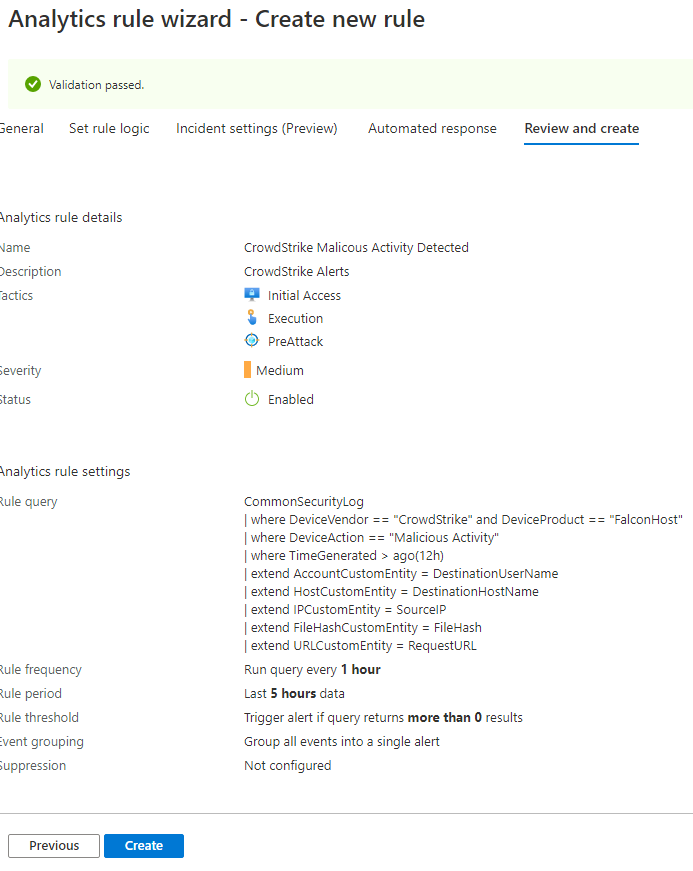
On the Review and Create tab Sentinel will validate the rule for any syntax errors or conflicts in the Rule. You need to click Create to generate the custom rule.
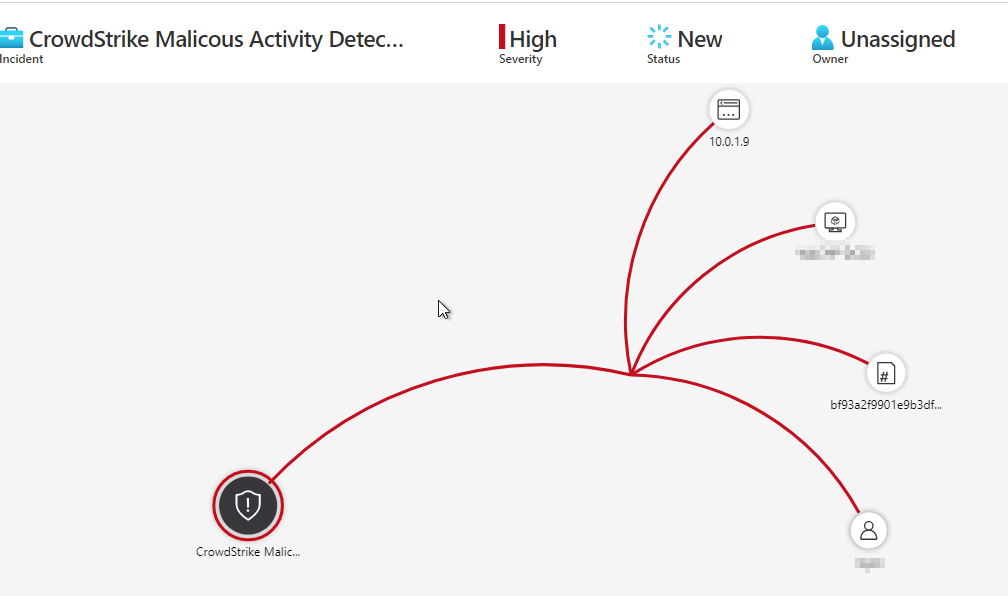
Now that you have the Analytics Rule in place, if you execute a test detection on a host, you should get an Incident in Sentinel. This will allow you to track your alerts in a central pane of glass and tie it to other incidents.
Automated Rule Deployment
If you’re automating your Sentinel deployments, you can import this Rule using the Wortel AzSentinel module. The Import-AzSentinelAlertRule function will import a JSON rule containing the logic.
Import-AzSentinelAlertRule -SubscriptionId "<subscription id>" -WorkspaceName "<workspace name>" -SettingsFile ".\Rules\CrowdStrikeDetections.json" -Verbose
{
"Scheduled": [
{
"displayName": "CrowdStrike Malicious Activity Detected",
"AlertRuleTemplateName": "",
"description": "This will alert when there is a CrowdStrike Falcon Detection.",
"severity": "High",
"enabled": true,
"query": "CommonSecurityLog | where DeviceVendor == \"CrowdStrike\" and DeviceProduct == \"FalconHost\" | where DeviceAction == \"Malicious Activity\" | where TimeGenerated > ago(12h) | extend AccountCustomEntity = DestinationUserName | extend HostCustomEntity = DestinationHostName | extend IPCustomEntity = SourceIP | extend FileHashCustomEntity = FileHash | extend URLCustomEntity = RequestURL",
"queryFrequency": "1H",
"queryPeriod": "5H",
"triggerOperator": "GreaterThan",
"triggerThreshold": 0,
"suppressionDuration": "6H",
"suppressionEnabled": false,
"tactics": [
"Execution",
"InitialAccess"
],
"playbookName": "logicapps-eus-pagerdutyalerts",
"aggregationKind": "SingleAlert",
"incidentConfiguration": {
"createIncident": true,
"groupingConfiguration": {
"enabled": false,
"reopenClosedIncident": false,
"lookbackDuration": "PT5H",
"entitiesMatchingMethod": "All",
"groupByEntities": [
"Account",
"Ip",
"Host",
"Url",
"FileHash"
]
}
}
}
]
}

Hey Byron,
You said, “Install the Azure Syslog Collector and configure the Data Replicator to forward to it.”
How do you configure the Falcon Data Replicator to send data to a syslog server? The links you provided are instructions for configuring the Crowdstrike SIEM collector to send data to Azure Syslog Collector.
The Crowdstrike SIEM collector and the Falcon Data Replicator are two different products.