It has been reported that 91% of data breaches were launched via a spear-phishing attack. For security professionals, it is widely known that email is the #1 attack vector used. But filtering and secure email gateways are oftentimes not enough to block a targeted spear-phishing attack.
Phishing simulations help your end-users identify phishing emails and how to respond to phishing emails in their mailbox correctly. Simulations and training are one of the most effective ways to deal with these dangerous types of attacks because they use real-world scenarios to replicate the sophisticated attacks that occur.
There are many phishing simulation services available such as KnowBe4 or Microsoft Attack Simulation Training, but these can be costly or require a premium upgrade in the case of Microsoft.
GoPhish
Gophish is an open-source attack simulation that allows pen testers or security organizations to generate real-world phishing attacks easily. And because it’s an open-source framework, it’s a solution that’s available to everyone. Gophish is well documented on their website and on Github. I’ll walk through installing and using Gophish, as well as some basic integrations with your other security tools.
The Gophish server binaries are available on GitHub for Linux, Windows, and macOS. You can also use Gophish via the official Docker container here.
Getting Started with GoPhish
Setting up and using GoPhish for phishing simulation is pretty straightforward, especially for an open-source solution. I’ll walk through the what’s needed in this article, but the steps involved are:
- Setup a Linux VM. I’m going to use a Ubuntu in Azure, but Windows can be used, as well as other cloud providers.
- Install GoPhish and other components.
- Configure GoPhish
- Setup your Phishing Simulation
Setup a GoPhish Virtual Machine
GoPhish has executables available for Windows, Linux, and Mac. GoPhish can also be deployed as a container. I set up a small Ubuntu VM in Azure for this exercise with 1 vCPU and 1 GB of RAM. You most likely will need to expose the Phishing Server to the Internet via 80/443, but you should keep SSH and the Admin Portal available via the Private IP of the VM.
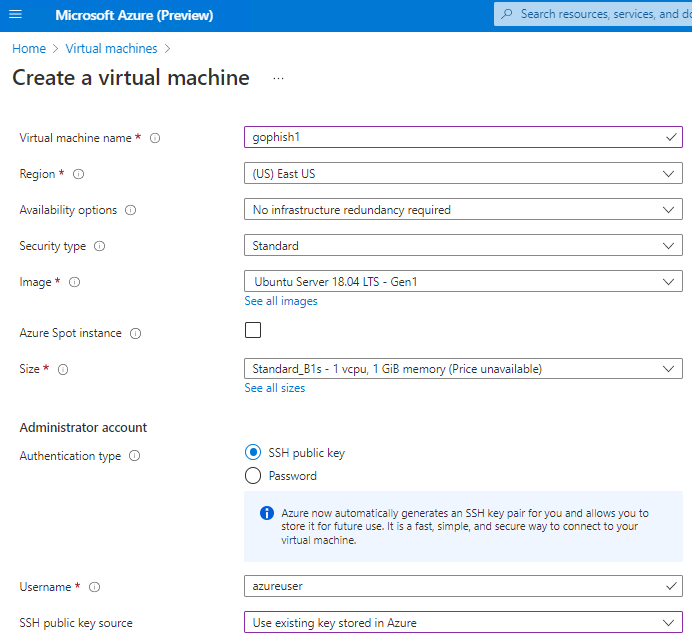
Once the VM is set up with a public IP address, configure a DNS record to point to the public IP address. I’ll use this later in the Phishing Campaign setup.
Install GoPhish
The GoPhish executables can be downloaded from Github. There are releases for the most popular operating systems.
SSH into the VM console using the credentials you created in Azure. You need to install a few prerequisite components first and then GoPhish.
Run the following command to install the Zip library.
apt-get install zip unzip
Run the following command to install the Sendmail SMTP server.
apt-get install sendmail
Run this command to configure Sendmail. Accept all defaults by pressing enter at each prompt.
sendmailconfig
Download the GoPhish executable and unzip it to an /opt directory.
wget https://github.com/gophish/gophish/releases/download/v0.11.0/gophish-v0.11.0-linux-64bit.zip
mkdir /opt/gophish
unzip /home/azureuser/gophish-v0.11.0-linux-64bit.zip -d /opt/gophish
Navigate to the /opt/gophish directory and create two sets of SSL Certs/Keys. One for the admin portal, and one for the phishing pages. To create a more mature setup, use certificates from a valid Certificate Authority.
openssl req -newkey rsa:2048 -nodes -keyout gophish-admin.key -x509 -days 365 -out gophish-admin.crt
openssl req -newkey rsa:2048 -nodes -keyout gophish.key -x509 -days 365 -out gophish.crt
Open the gophish configuration and update the certificate settings to point to the cert files you made. Also update the admin_server listen_url to match your VM’s private IP.
{
“admin_server”: {
“listen_url”: “10.0.0.9:3333”,
“use_tls”: true,
“cert_path”: “gophish-admin.crt”,
“key_path”: “gophish-admin.key”
},
“phish_server”: {
“listen_url”: “0.0.0.0:80”,
“use_tls”: false,
“cert_path”: “gophish.crt”,
“key_path”: “gophish.key”
},
“db_name”: “sqlite3”,
“db_path”: “gophish.db”,
“migrations_prefix”: “db/db_”,
“contact_address”: “”,
“logging”: {
“filename”: “”,
“level”: “”
}
}
Run the following command to make the Gophish executable able to be executed.
chmod +x Gophish
Now run this command to launch Gophish from your /opt/gophish directory.
./gophish
You should be able to browse to the Admin Portal using private IP address you defined for the VM.
Log into the Admin portal using the credentials that are displayed when launched the execuatable.
Setting up your Phishing Campaign
GoPhish is pretty simple to set up, but allows for some complex customizations. There are a few basic steps needed before you can send your first email. In my scenario, I setup a Phishing Campaign to mimic a Heroku Email Reset email with a cloned Heroku login page.
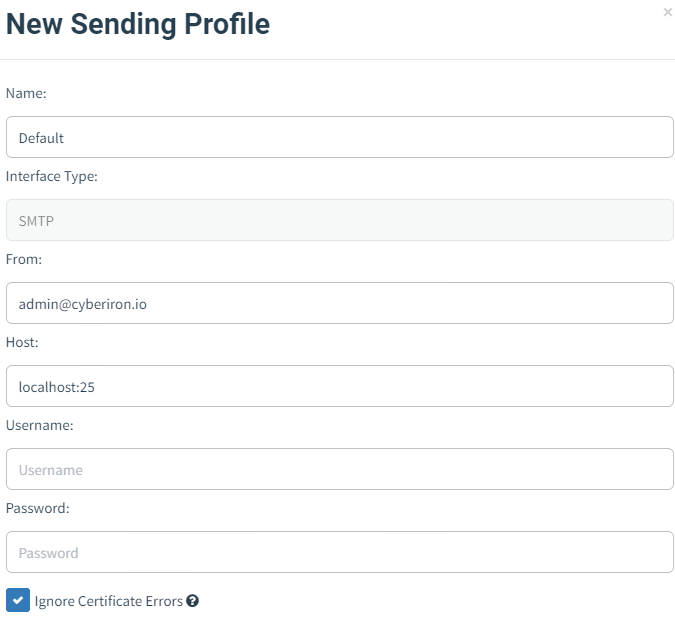
Configure the Sending Profile
The Sending Profile defines the SMTP connection details and the From address.
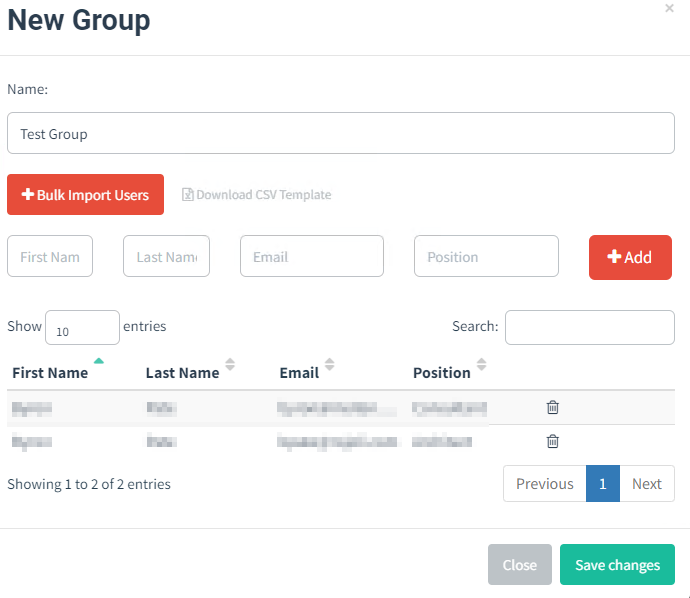
Create a User Group
User Groups contain the target email addresses for your phishing campaign. You can bulk import a CSV or directly enter the contact details.
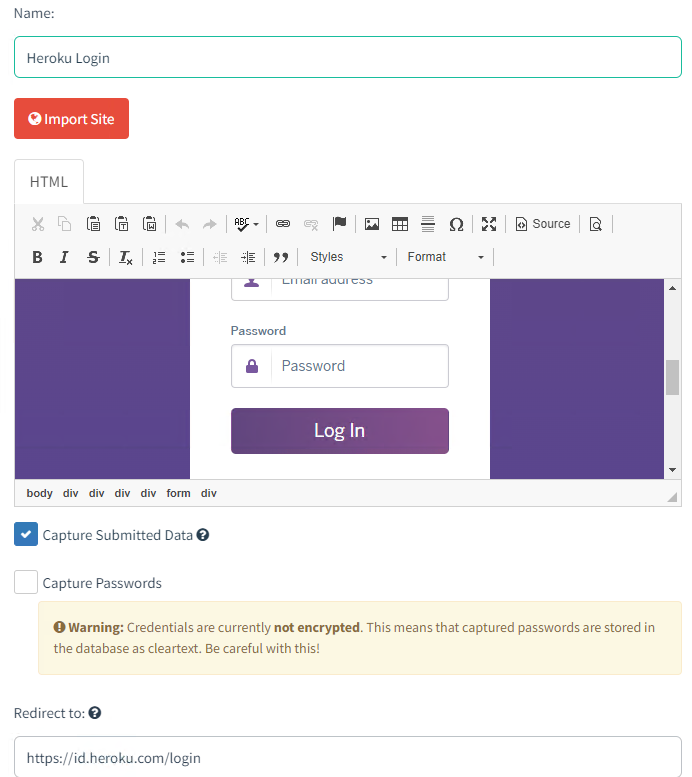
Create a Landing Page
The landing page is where you’ll actually collect credentials. One of the great features of GoPhish is that you can point at an existing URL and GoPhish will copy the HTML into you page. This is really easy, but it also works extremely well. In my case I used the Heroku Login Page. You can also configure the Landing Page to collect submitted data.
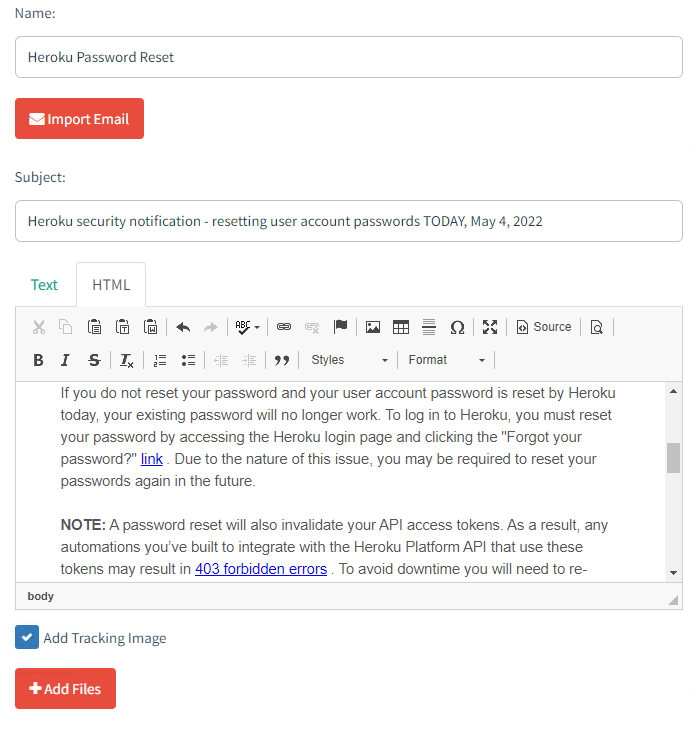
Create an Email Template
The phishing emails you can send out are defined in Email Templates. You can manually write the email yourself or use the Import Email function to copy/paste a raw email body. Again using the Import feature allows you to duplicate realistic emails.
Create the Campaign
The GoPhish Campaign ties all the other components together and sends out the phishing email to users. In the URL field use the DNS address that points to the public IP address of the VM. This will be used to host the landing page that users will be sent to.
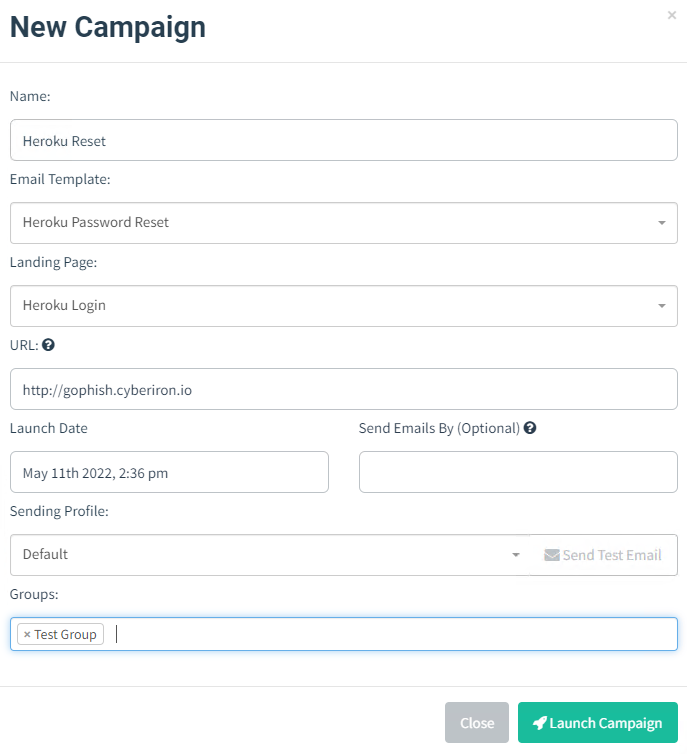
Results
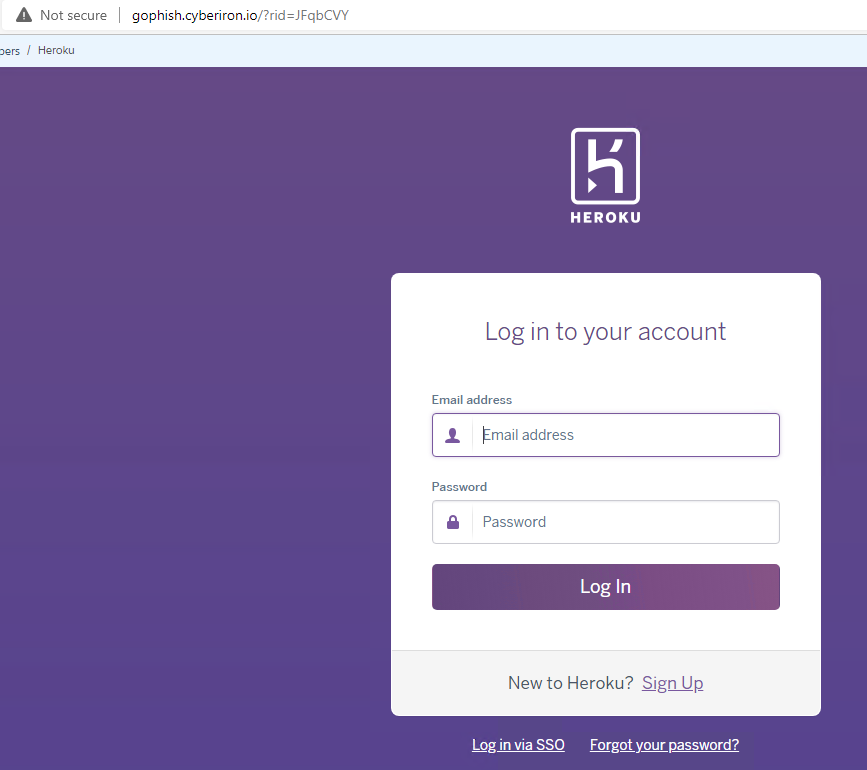
The email links will send the user to the landing page we created on the GoPhish VM.
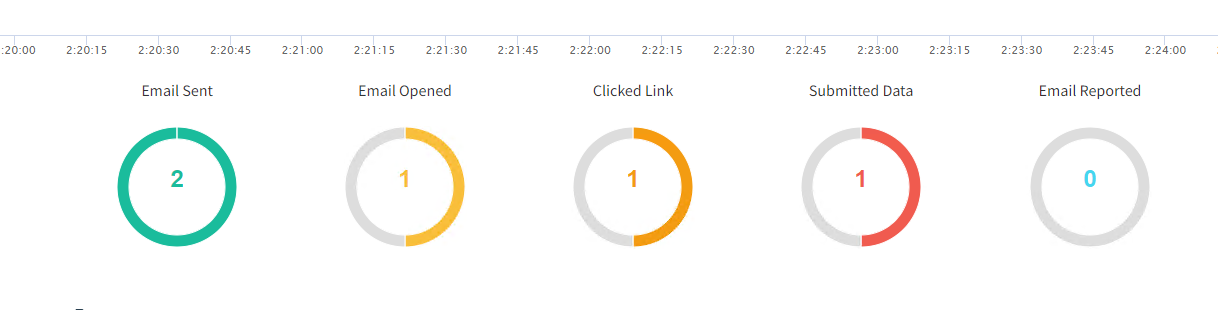
On the GoPhish dashboard, we can see results in real-time, and track the progress of our campaign.
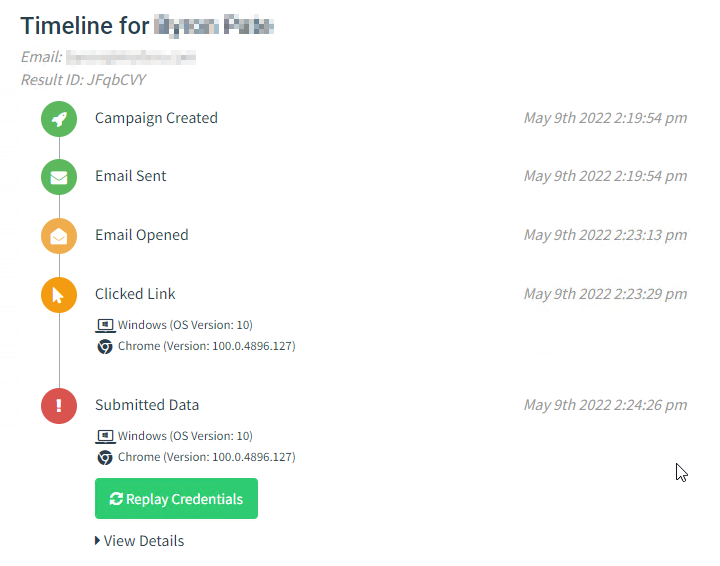
We can drill into the activity for a user and see the timeline and captured credentials.
Summary
GoPhish clearly provides a solid alternative to commercial phishing simulations for training or red team operations. The UI is very easy to navigate and also provides a very strong tool for building phishing campaigns. GoPhish already has a number of integrations with other commercial tools and modifications.
