In recent months, COVID-19 has accelerated trends in business and technology that were already in motion. The great shift of employees to work-from-home has hastened the shift to SaaS. Microsoft 365, Power BI, Dynamics, and Azure are some of the most popular clouds for businesses. Azure provides the underlying platform to this software. But for the majority of businesses, properly hardening Azure does not happen. Organizations can take a few steps to implement security hardening that will greatly reduce risk. The following Azure configurations to prevent attacks and monitor for attacks.
- Harden Azure Active Directory
- Conditional Access Rules
- Security Center
- Azure Sentinel
- Preview Configurations
Harden Azure Active Directory
Azure Active Directory provides the Identity Provider for all Microsoft Services. It uses much of the same concepts as Active Directory servers. There are many functions available in Azure Active Directory and as a result many relevant security configurations. Administrators can configure the following settings within Azure Active Directory to harden authorization and authentication.
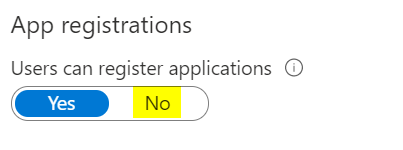
Disable App Registrations
Location: Azure AD > User Settings > Users can register applications
This disables users from registering Azure AD applications. Only administrators should perform this action.
Change from Yes (default) to No.
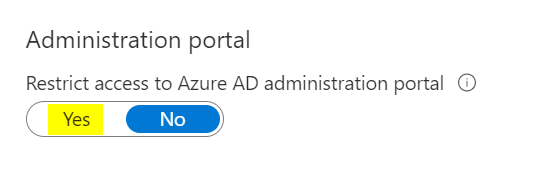
Restrict Access to Azure Portal
Location: Azure AD > User Settings > Restrict access to Azure AD administration portal
This is another important setting, which limits access to the Azure AD admin portal to administrators. This prevents users from viewing sensitive details about your organization and aligns with the principal of least privileged access.
Change from No (default) to Yes
Restrict LinkedIn Accounts
Location: Azure AD > User Settings > LinkedIn Account Connections
Thihs setting allows linking Azure AD accounts to LinkedIn. This is rarely needed in most organizations, and poses a data loss risk.
Change from Yes (default) to No.

Guest User Access
Location: Azure AD > User Settings > Manage external collaboration settings> Guest user access
This setting limits the permissions that a Guest account has within Azure AD. The recommendation is to limit their access to only view their own objects. This prevents reconnaissance activity.
Change to Guest user is access is restricted.

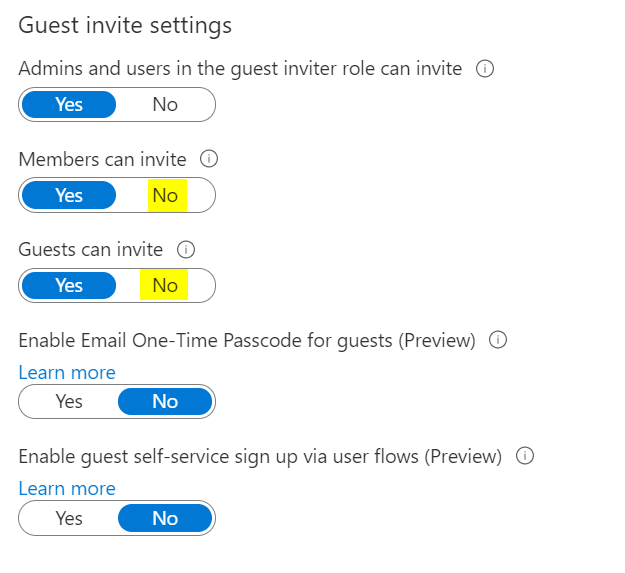
Guest Invite Settings
Location: Azure AD > User Settings > Manage external collaboration settings> Guest invite settings
These settings control who can invite Guests into Azure AD. Disabling Guests from inviting other Guests should be a priority. But preferrably only Admins or users delegate the role can send invitations. This helps prevent the creation of back door accounts into your tenant.
Change Members can invite from Yes (default) to No.
Chane Guests can invite from Yes (default) to No.
Restrict Invitations
Location: Azure AD > User Settings > Manage external collaboration settings> Collaboration restrictions
This setting restricts who can be invited into your Azure AD as a Guest. Only specific domain names are specified that members can invite.
Change to Allow invitations only to the specified domains.

Conditional Access Rules
Conditional Access Rules are used to enforce Multi-Factor Authentication and granular authorization rules. Different components of the user’s session, such as location, device posture, and group membership are used to apply restrictions. Conditional Access Rules do require that users are licensed with an Azure AD Premium P1 license.
Use the following Conditional Access Rules to lock down access. Navigate to Azure AD > Security > Conditional Access
MFA for All
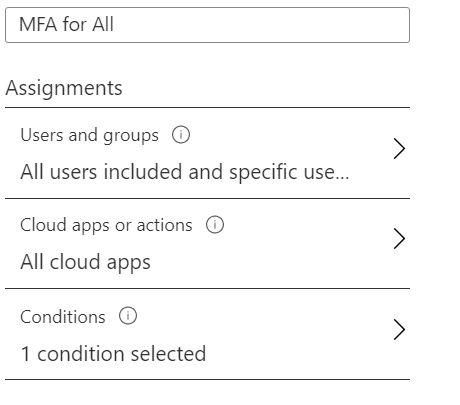
Enable MFA for all users. This is an effective policy to prevent account take over for most users.
- Users and Groups: All Users
- Cloud Apps: All cloud apps
- Conditions: Client Apps – Browser, Mobile Apps and Desktop Clients.
- Access Controls: Grant Access – Require multi-factor authentication.

Block Legacy Authentication
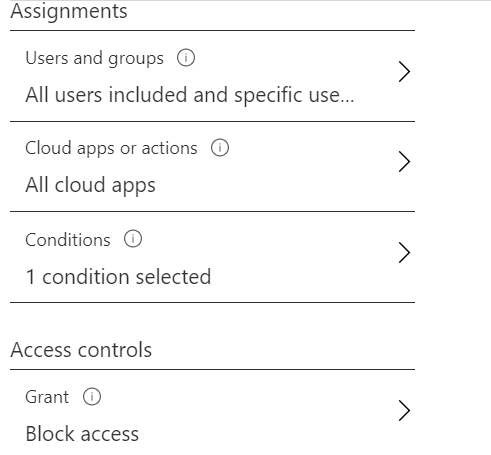
Prevent users from using vulnerable protocols to authenticate.
- Users and Groups: All Users
- Cloud Apps: All cloud apps
- Conditions: Client Apps – Other
- Access Controls: Block Access
Block by Location
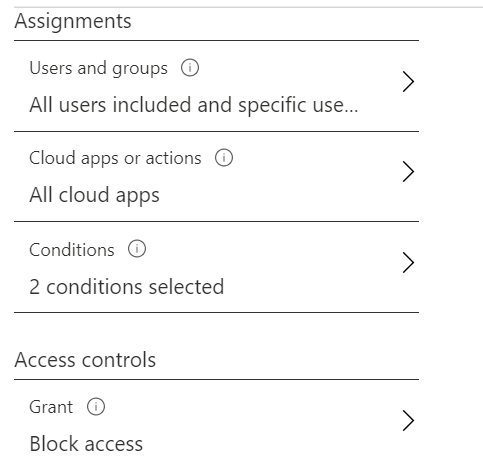
Use this policy to block logins from countries that your users never travel to. If the organization only has users in a certain region, it’s pretty safe to block most other countries.
- Users and Groups: All Users
- Cloud Apps: All cloud apps
- Conditions: Locations – Blocked Countries list, Client Apps – Browser, Mobile Apps and Desktop Clients.
- Access Controls: Block Access
If you want more detail on this control, see my detailed article on implementing it.
Enforce MFA for Admins
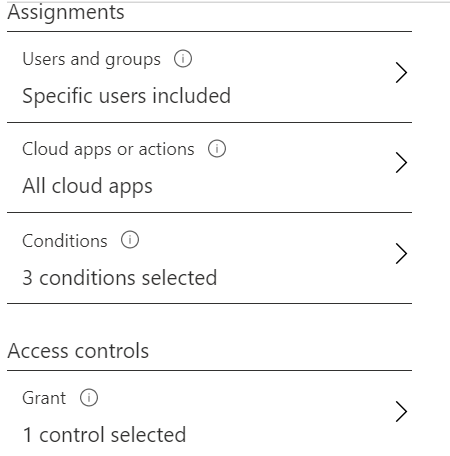
Ensure all users with an Admin role must use multi-factor authentication.
- Users and Groups: Specific Groups – Select all Admin Groups
- Cloud Apps: All cloud apps
- Conditions: Any device, Any location, All Client Apps – Browser, Mobile Apps and Desktop Clients.
- Access Controls: Grant Access – Require multi-factor authentication.
Security Center
Security Center contains configuration vulnerability reporting and threat detection alerts. It’s a good idea to enable the Standard Tier and disable the unused components unless you have a 3rd party Cloud Security Posture Management (CSPM) service in use.
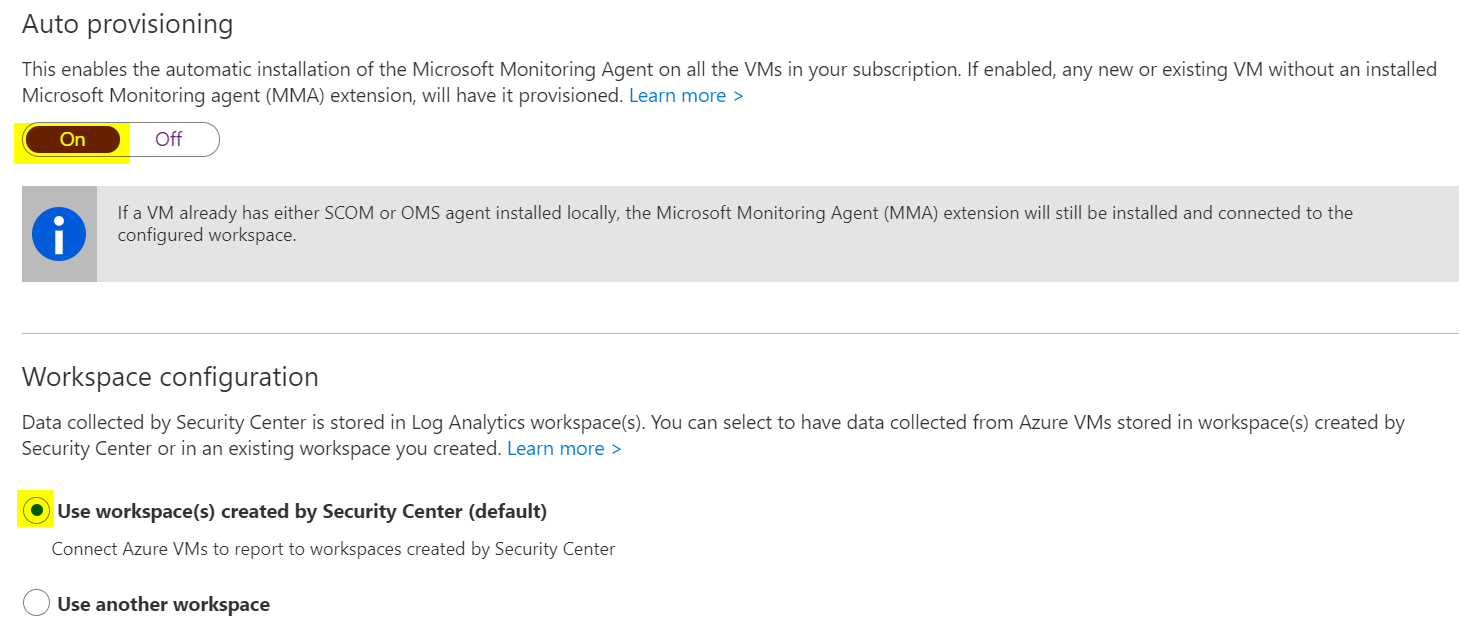
Auto Provision Monitoring Agents
Location: Security Center > Pricing & Setting > Data Collection
This setting will cause the Microsoft Monitoring Agent to be installed automatically on all virtual machines in your environment. The event data will be pushed to a Log Analytics Workspace. This is a really simple way to centralize event collection for security purposes.
Change the Auto provisioning from Off (default) to On. Use workspace created for Security Center.
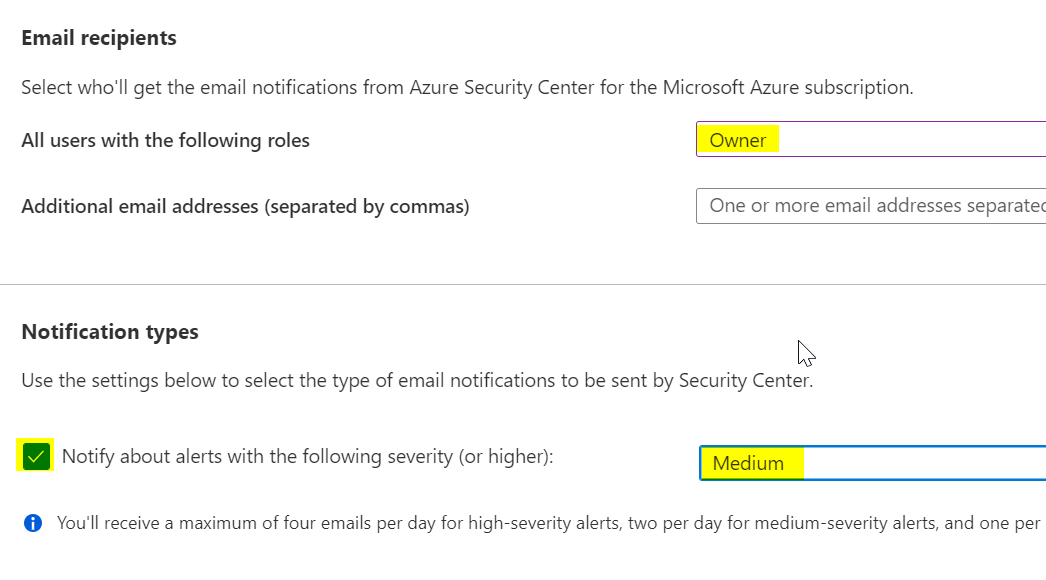
Enable Email Alerts
Location: Security Center > Pricing & Setting > Email Notifications
Security Center allows you to enable Email Notifications of configuration vulnerabilities. If you have thousands of deployed assets, this may not be a good solution for Posture Management, but for small Azure environments, this is a good way to stay on top of vulnerabilities. Use this to configure alerts about configuration vulnerabilities. An alternative is to configure a Logic App to push alerts into an Incident Management system.

Enable Automation Integration
Location: Security Center > Pricing & Setting > Workflow automation
Add workflow automations to integrate alerts with other incident management tools. You can configure Logic Apps to push alerts to email or more complex workflows like Service Now or PagerDuty.
Azure Sentinel
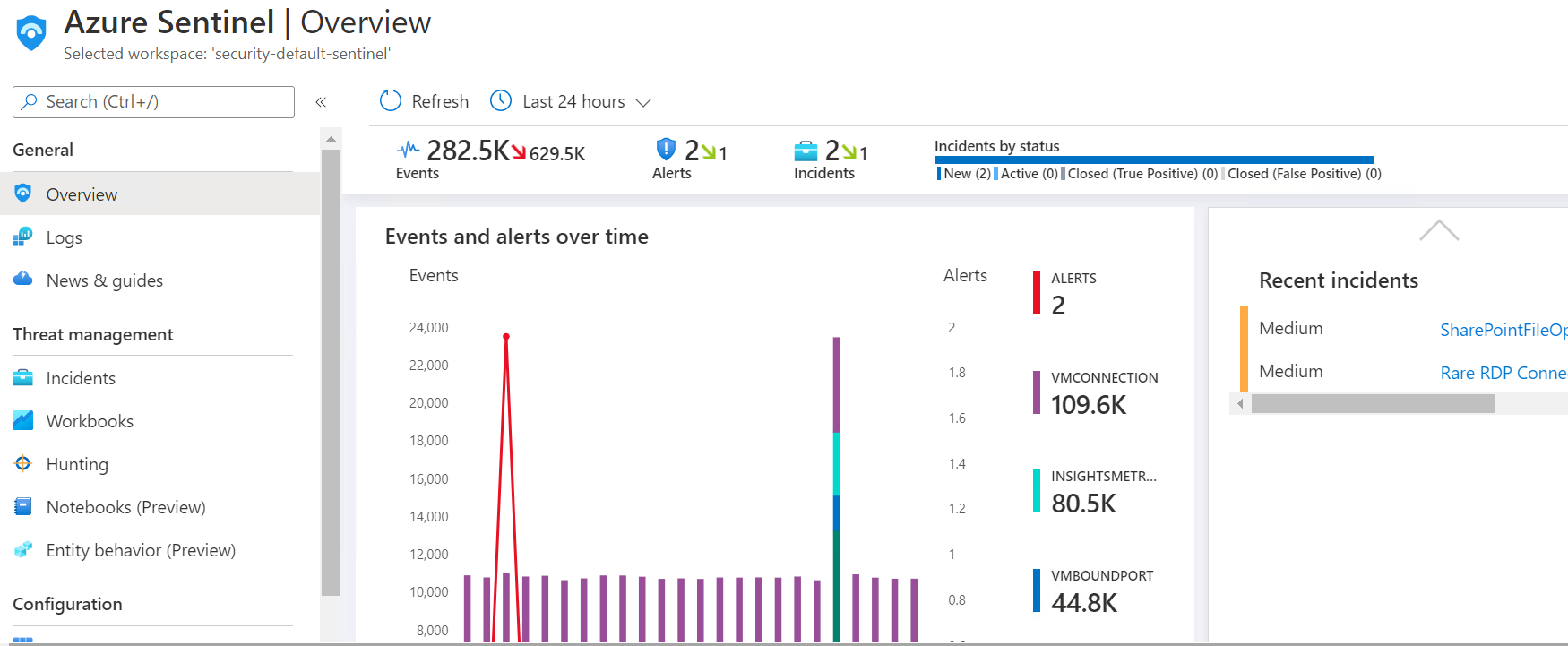
Azure Sentinel provides a native Cloud Detection and Response function for Microsoft 365 and Azure customers. Sentinel will correlate and match events against out of the box or custom events. This provides a way to detect malicious activity in Office, SharePoint, Teams, and Azure services. Enable the following Data Sources to collect standard events.
- Azure Active Directory
- Azure Active Directory Identity Protection
- Azure Activity
- Azure Information Protection (Preview)
- Azure Security Center
- Azure Web Application Firewall (WAF)
- DNS (Preview)
- Microsoft Cloud App Security
- Office 365
- Office 365 Advanced Threat Protection (Preview)
- Security Events
- Windows Firewall
Azure Sentinel has much more configurations that can be applied that are beyond the scope of this article, so I would recommend doing more research and testing with Sentinel.
Preview Configurations
The following are not currently in General Availability but can be accessed via the Preview Portal.
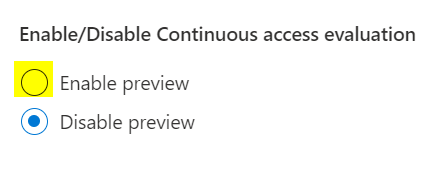
Enable Continue Access Evaluation
Location: Azure AD > Security > Continuous access evaluation
Change from Disable Preview (default) to Enable preview
Summary
This article provides a good overview of configurations that most administrators can apply to Microsoft 365 and Azure to reduce information security risk and further tighten security controls. We expect that attacks against these platforms will only continue to rise in the coming months, so these steps are important for your security program.
